Communications of the ACM

The blog archive provides access to past blog postings from Communications of the ACM and other sources by date.
January 2020
From Schneier on Security
Friday Squid Blogging: The Pterosaur Ate Squid

New research: "Pterosaurs ate soft-bodied cephalopods (Coleiodea)." News article. As usual, you can also use this squid post to talk about the security stories in the news that I haven't covered. Read my blog posting guidelines…
From The Eponymous Pickle
Online Communications of the ACM

I was reminded that there is an online version of the CACM magazine, which contains many of its articles, Here it is for the February issue.
From Schneier on Security
NSA Security Awareness Posters

From a FOIA request, over a hundred old NSA security awareness posters. Here are the BBC's favorites. Here are Motherboard's favorites. I have a related personal story. Back in 1993, during the first Crypto Wars, I and a handful…
From The Eponymous Pickle
Why is Amazon Dominating the Market?

Amazon continues to thrive. What is driving them in retail?
These 3 Numbers Explain Why Amazon Is Dominating Everything Right Now
Amazon reported earnings on Thursday, and clearly investors were happy. In after-hours trading,…
From insideHPC
New FLAIR Protocol to Speed Computer Networks

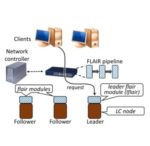 Computer scientists at the University of Waterloo have found a novel approach that significantly improves the storage efficiency and output speed of computer systems. “Since the invention of computers, networks that connect storage…
Computer scientists at the University of Waterloo have found a novel approach that significantly improves the storage efficiency and output speed of computer systems. “Since the invention of computers, networks that connect storage…
From insideHPC
Building a Federated Research Collaborative

 In this special guest feature, David Fellinger from the iRODS Consortium writes that the secure federation capabilities of iRODS has changed the way that we think of data locality. The concept of countrywide and worldwide research…
In this special guest feature, David Fellinger from the iRODS Consortium writes that the secure federation capabilities of iRODS has changed the way that we think of data locality. The concept of countrywide and worldwide research…
From insideHPC
WekaIO picks up steam in the HPC Market

 Today WekaIO announced it closed its 2019 fiscal year with record velocity in revenues. The company grew revenue by 600% compared to 2018 with growth fueled by increasing adoption of NVMe-native storage systems to enable I/O-intensive…
Today WekaIO announced it closed its 2019 fiscal year with record velocity in revenues. The company grew revenue by 600% compared to 2018 with growth fueled by increasing adoption of NVMe-native storage systems to enable I/O-intensive…
From insideHPC
Video: Open and High Performance Computing

 Hugh Blemings from the OpenPOWER Foundation gave this talk at the Linux.Conf.au conference. "This session will explain the importance of open hardware and software at all levels of the compute environment - embedded/IoT to desktop…
Hugh Blemings from the OpenPOWER Foundation gave this talk at the Linux.Conf.au conference. "This session will explain the importance of open hardware and software at all levels of the compute environment - embedded/IoT to desktop…
From The Eponymous Pickle
DNA Based Archival Storage

Seems a strange idea, but its a look at forms of data, like DNA and the needs for computing. A form of biomimicry.
$25M Project Will Advance DNA-Based Archival Data Storage
Georgia Tech Research Horizons
By John Toon
January 16,…
From The Eponymous Pickle
Swarming Defense Drones

Drones by their more flexible nature are creating new options with different kinds of precision, scale and application. Here a Defense example.
DARPA is testing drones it can launch from a plane—then collect mid-air in MIT Technology…
From The Eponymous Pickle
Top ACM Technews Articles of 2019

A group I have written for for over a decade, and who I have a member of for much longer. Kept me up to date in many ways. They gather, distribute and expand lots of emergent tech ideas that use computing, and I have been…
From Schneier on Security
U.S. Department of Interior Grounding All Drones

The Department of Interior is grounding all non-emergency drones due to security concerns: The order comes amid a spate of warnings and bans at multiple government agencies, including the Department of Defense, about possible…
From BLOG@CACM
The Vote as a Declared Datum

A vote is a datum that sheds its original identity but persists.
From Daniel Lemire's Blog
Cost of a thread in C++ under Linux

Almost all our computers are made of several processing cores. Thus it can be efficient to “parallelize” expensive processing in a multicore manner. That is, instead of using a single core to do all of the work, you divide the…
From The Eponymous Pickle
Aiming to Dupe AntiFraud Systems: Digital Doppelgangers

Quite an interesting discovery. Constructing fake user profiles to facilitate fraud. Goes back to the need for stronger means of constructing foolproof real identities, probably cryptographically determined. 'Fraud on Demand'…
From The Eponymous Pickle
Avast Shutters Jumpshot

Followed this because of recent revelations and our look at data as an asset. At one time had been using Avast.
Avast shutters data-selling subsidiary amid user outrage
Users were not happy to learn "security" software sold their…
From The Eponymous Pickle
McKinsey on Future of Work

Some good comments on future of work.
Getting Practical About the Future of Work
January 2020 | Article
By Bryan Hancock, Kate Lazaroff-Puck, and Scott Rutherford
Article (PDF-689KB)
What story will people tell about your organization…
From The Computing Community Consortium Blog
CCC Workshop Report- Content Generation for Workforce Training

The Computing Community Consortium (CCC) is pleased to announce the release of a new CCC workshop report called Content Generation for Workforce Training. This report is based on presentations and discussions at the CCC workshop…
From insideHPC
ECP Report: Advancing Scientific Productivity through Better Scientific Software

 The Exascale Computing Project has published a new report to foster and advance software productivity and sustainability for extreme-scale computational science. The report introduces work by the IDEAS-ECP project, explaining…
The Exascale Computing Project has published a new report to foster and advance software productivity and sustainability for extreme-scale computational science. The report introduces work by the IDEAS-ECP project, explaining…
From insideHPC
Argonne to Deploy Cray ClusterStor E1000 Storage System for Exascale

 Today HPE announced that ALCF will deploy the new Cray ClusterStor E1000 as its parallel storage solution. The new collaboration supports ALCF’s scientific research in areas such as earthquake seismic activity, aerospace turbulence…
Today HPE announced that ALCF will deploy the new Cray ClusterStor E1000 as its parallel storage solution. The new collaboration supports ALCF’s scientific research in areas such as earthquake seismic activity, aerospace turbulence…
From insideHPC
Quantum Computing Inc. Releases Mukai Quantum Development Platform

 Today Quantum Computing Inc. announced its Mukai quantum application development platform. Focused on developing novel quantum applications, the Company is leveraging their collective expertise in finance, computing, security…
Today Quantum Computing Inc. announced its Mukai quantum application development platform. Focused on developing novel quantum applications, the Company is leveraging their collective expertise in finance, computing, security…
From insideHPC
Podcast: The Trouble with ZFS

 In this podcast, the Radio Free HPC team discuss whether ZFS is ever going to meet its potential. "Henry weighs in on the evolution of ZFS and how his opinion of ZFS has changed over the last decade or so. Both Shahin and Henry…
In this podcast, the Radio Free HPC team discuss whether ZFS is ever going to meet its potential. "Henry weighs in on the evolution of ZFS and how his opinion of ZFS has changed over the last decade or so. Both Shahin and Henry…
From insideHPC
Video: Making Supernovae with Jets

 Chelsea Harris from the University of Michigan gave this talk at the CSGF 2019. "I am developing a FLASH hydrodynamics module, SparkJoy, to perform these simulations at high order. These projects are part of a DOE INCITE project…
Chelsea Harris from the University of Michigan gave this talk at the CSGF 2019. "I am developing a FLASH hydrodynamics module, SparkJoy, to perform these simulations at high order. These projects are part of a DOE INCITE project…
From Schneier on Security
Collating Hacked Data Sets

Two Harvard undergraduates completed a project where they went out on the Dark Web and found a bunch of stolen datasets. Then they correlated all the information, and then combined it with additional, publicly available information…
From The Eponymous Pickle
Fuzzing for Testing Security Vulnerabilities

Of interest from Communications of the ACM:
"Fuzzing: Hack, Art, and Science," by Patrice Godefroid, recommends fuzz testing to detect security vulnerabilities in software. Godefroid describes three core fuzzing techniques in
Fuzzing…
From The Eponymous Pickle
Web Scraping is now Legal

Should be considerable changes in behavior for certain kinds of data. Still some trguation about crawling in this way.
Web scraping is now legal
Here’s what that means for Data Scientists
By Tom Waterman in Towards Data Science…
From The Eponymous Pickle
Man Diagnosed with Coronavirus Treated Largely by Robot

Achieving isolation for treatment appears to the primary goal.
Man Diagnosed with Wuhan Coronavirus Is Being Treated Largely by a Robot
CNN by Nicole Chavez
The first person diagnosed with the Wuhan coronavirus in the U.S. is being…
From The Computing Community Consortium Blog
Great Innovative Idea: Revolutionizing Tree Management via Innovative Spatial Techniques

The following great innovative idea is from Yiqun Xie, who is a Ph.D. candidate at the University of Minnesota. Xie along with his advisor and former Computing Community Consortium (CCC) Council member McKnight Distinguished…
From The Eponymous Pickle
Eclipse Foundation for Open Inno and Collaboration

Eclipse Foundation
The Platform for Open Innovation and Collaboration
The Eclipse Foundation provides our global community of individuals and organizations with a mature, scalable and commercially-friendly environment for open…
From insideHPC
Indiana University Launches Quantum Science and Engineering Center

 Indiana University has launched a Quantum Science and Engineering Center. The new center will investigate possibilities created by the strange properties of quantum theory, particularly the phenomenon known as quantum entanglement…
Indiana University has launched a Quantum Science and Engineering Center. The new center will investigate possibilities created by the strange properties of quantum theory, particularly the phenomenon known as quantum entanglement…
