Communications of the ACM

The blog archive provides access to past blog postings from Communications of the ACM and other sources by date.
March 2019
From The Eponymous Pickle
A Look at Digital Buttons: Amazon Dash

Below is the first piece in TheVerge on 'Buttons', which I loosely define as simple as possible interfaces to otherwise complex processes. Probably the best known is the Amazon Dash. I remember discussing it with folks from…
From insideHPC
Video: How Deep Learning Could Predict Weather Events

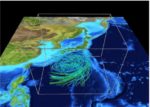 Seongchan Kim from KISTI gave this talk at GTC 2019. "How do meteorologists predict weather or weather events such as hurricanes, typhoons, and heavy rain? Predicting weather events were done based on supercomputer (HPC) simulations…
Seongchan Kim from KISTI gave this talk at GTC 2019. "How do meteorologists predict weather or weather events such as hurricanes, typhoons, and heavy rain? Predicting weather events were done based on supercomputer (HPC) simulations…
From insideHPC
AFRL Unveils Sharable Classified Supercomputing Capability

 The Air Force Research Laboratory has unveiled the first-ever shared classified Department of Defense high performance computing capability at the AFRL DOD Supercomputing Resource Center. "The ability to share supercomputers
…
The Air Force Research Laboratory has unveiled the first-ever shared classified Department of Defense high performance computing capability at the AFRL DOD Supercomputing Resource Center. "The ability to share supercomputers
…
From The Eponymous Pickle
Supply Chain by the Numbers

Thought provoking numbers from the industry
Supply Chain by the Numbers from Supply Chain Digest
Supply Chain by the Numbers for March 28, 2019
Wisconsin Paper Mill gets Second Life; UPS First Revenue-Generating Drone…
From The Eponymous Pickle
Gestures, Perception and Meaning

Long followed gesture as alternate interface, is it far beyond that?
How the Brain Links Gestures, Perception and Meaning in QuantaMagazine
Neuroscience has found that gestures are not merely important as tools of expression but…
From Putting People First
Research findings send automated sentiment analysis to the trash bin

![]() The age of social media has opened up exciting opportunities for researchers to investigate people’s emotional states on a massive scale. For example, one study found that tweets contain more positive emotional words in the morning…
The age of social media has opened up exciting opportunities for researchers to investigate people’s emotional states on a massive scale. For example, one study found that tweets contain more positive emotional words in the morning…
From Putting People First
Time Change: How the UX of Time Begins Below the UI

The user experience of most web-based applications begins well below the interface, all the way down to fields in a database. Examining how systems and users experience time prove this point dramatically. Think about how messy…
From The Eponymous Pickle
Discovering Contracts

The idea of 'discovering' contracts struck me. Take it further to discovering agreements embedded in text. Does not have to be as complex as 'legal' contracts. Takes it beyond to the the discovery of the implications of…
From The Eponymous Pickle
Scenarios for the Future of Work

As usual excellent pointers to learning in this area.
Via the O'Reilly Next Economy Newsletter
4 scenarios for the future of work (70+ page PDF)
Based on a methodology called morphological analysis, new research from the UK’s Royal…
From The Eponymous Pickle
AI is Transforming Marketing

Very good overview piece on marketing and AI in CustomerThink. Intro is below. Statistics they gathered are also interesting:
Artificial Intelligence Is Transforming Digital Marketing And For Good Reason! By Evan Brown …
From BLOG@CACM
The Artificialistic Fallacy

Ethics discussions of artificial intelligence reveal a fallacy of omission.
From The Eponymous Pickle
Google Shuts Down Fusion Tables

More criticism for Google ditching tests. Here one that has been around for some time. I recall looking at and recommending it for a trial. Certainly promotes your cloud. This was an impressive visualization service. I…
From insideHPC
Amazon Elastic Fabric Adapter: Anatomy, Capabilities, and the Road Ahead

 Raghu Raja from Amazon gave this talk at the OpenFabrics Workshop in Austin. "Elastic Fabric Adapter (EFA) is the recently announced HPC networking offering from Amazon for EC2 instances. It allows applications such as MPI to…
Raghu Raja from Amazon gave this talk at the OpenFabrics Workshop in Austin. "Elastic Fabric Adapter (EFA) is the recently announced HPC networking offering from Amazon for EC2 instances. It allows applications such as MPI to…
From insideHPC
Job of the Week: Senior HPC Systems Engineer at Children’s Mercy Hospital

 Children's Mercy Hospital in Kansas City is seeking a Senior HPC Systems Engineer in our Job of the Week. "A Senior HPC Systems Engineer is responsible for the daily operation and monitoring of a high performance computing infrastructure…
Children's Mercy Hospital in Kansas City is seeking a Senior HPC Systems Engineer in our Job of the Week. "A Senior HPC Systems Engineer is responsible for the daily operation and monitoring of a high performance computing infrastructure…
From Daniel Lemire's Blog
Science and Technology links (March 30th 2019)

As we age, we accumulate old and useless (senescent) cells. These cells should die, but they do not. Palmer et al. removed senescent cells in obese mice. They found that these mice were less diabetic and just generally healthier…
From The Eponymous Pickle
Sources of Marketing Data

Interesting challenge, made me think about sources of information and their value. Recently talked to companies about this problem and solutions.
Instead of surveillance, what if we told advertisers what they wanted to know?
Companies…
From The Eponymous Pickle
Driving Information Diffusion

Never thought it was just about central users, but it helps to create uniformly consistent reactions.
Even Central Users Do Not Always Drive Information Diffusion
By Chao Gao, Zhen Su, Jiming Liu, Jürgen Kurths
Communications…
From Schneier on Security
Friday Squid Blogging: Restoring the Giant Squid at the Museum of Natural History

It is traveling to Paris. As usual, you can also use this squid post to talk about the security stories in the news that I haven't covered. Read my blog posting guidelines here....
From The Eponymous Pickle
AI in the Fresh Supply Chain

Colleagues speak on this application, ts hard because Fresh is hard to to replenish effectively. And people like myself who are avid cooks like a diverse selection. First thing I look at in a new Grocery is what do they have…
From The Eponymous Pickle
Smart Contracts as BlockChains Killer App?

Still quit a bit to achieve to make smart contracts clear and understandable. Smart contracts can be embodied in any code, but code can be prone to error depending on context. Note point on the 'intent of the code'. The
Smart…
From The Eponymous Pickle
Open Source Code to Extract Sensor Insights

Ultimately all analytics and AI is about extracting insights from sensors and productively re-using them. So any way to speed up the prototyping of that process is useful. Especially useful if you already use Matlab.
Open Source…
From insideHPC
Inspur to Offer BeeGFS Storage Systems for HPC and AI Clusters

 Today Inspur announced that it will offer integrated storage solutions with the BeeGFS filesystem. BeeGFS, a leading parallel cluster file system with a distributed metadata architecture, has gained global acclaim for its usability…
Today Inspur announced that it will offer integrated storage solutions with the BeeGFS filesystem. BeeGFS, a leading parallel cluster file system with a distributed metadata architecture, has gained global acclaim for its usability…
From insideHPC
NVIDIA GPUs Speed Altair OptiStruct structural analysis up to 10x

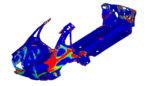 Last week at GTC, Altair announced that it has achieved up to 10x speedups with the Altair OptiStruct structural analysis solver on NVIDIA GPU-accelerated system architecture — with no compromise in accuracy. This speed boost…
Last week at GTC, Altair announced that it has achieved up to 10x speedups with the Altair OptiStruct structural analysis solver on NVIDIA GPU-accelerated system architecture — with no compromise in accuracy. This speed boost…
From insideHPC
Agenda Posted for MSST Mass Storage Conference in May

 The Massive Storage Systems and Technology Conference (MSST) posted their preliminary speaker agenda. Keynote speakers include Margo Seltzer and Mark Kryder, along with a five-day agenda of invited and peer research talks and…
The Massive Storage Systems and Technology Conference (MSST) posted their preliminary speaker agenda. Keynote speakers include Margo Seltzer and Mark Kryder, along with a five-day agenda of invited and peer research talks and…
From BLOG@CACM
An Agile Approach to Learning Programming

The Super Simple Programming Book is one example to teach programming in an Agile way. In general, Agile concepts can lead to highly effective learning.
From insideHPC
Big Compute Podcast: Accelerating HPC Workflows with AI

 In this Big Compute Podcast, Gabriel Broner from Rescale and Dave Turek from IBM discuss how AI enables the acceleration of HPC workflows. "HPC can benefit from AI techniques. One area of opportunity is to augment what people…
In this Big Compute Podcast, Gabriel Broner from Rescale and Dave Turek from IBM discuss how AI enables the acceleration of HPC workflows. "HPC can benefit from AI techniques. One area of opportunity is to augment what people…
From insideHPC
Video: DDN Accelerates Ai, Analytics, and Deep Learning at GTC

 In this video from the 2019 GPU Technology Conference, James Coomer from DDN describes the company's high-speed storage solutions for Ai, Machine Learning, and HPC. "This week at GTC, DDN is showcasing its high speed storage
…
In this video from the 2019 GPU Technology Conference, James Coomer from DDN describes the company's high-speed storage solutions for Ai, Machine Learning, and HPC. "This week at GTC, DDN is showcasing its high speed storage
…
From The Eponymous Pickle
Podcast: Business, Disruption and Technology

Harvard professor Thales Teixeira explains why customer behavior, not technology, ultimately drives disruption.
The emergence of a new technology is often cited as what drives the disruption of an industry or business. But that…
From Gödel's Lost Letter and P=NP
Integer Multiplication in NlogN Time
A win for multi-variable polynomials Composite crop from src1, src2 David Harvey and Joris van der Hoeven are computational mathematicians. They have just released a paper showing how to multiply two -bit integers in time. A…
From Schneier on Security
NSA-Inspired Vulnerability Found in Huawei Laptops

This is an interesting story of a serious vulnerability in a Huawei driver that Microsoft found. The vulnerability is similar in style to the NSA's DOUBLEPULSAR that was leaked by the Shadow Brokers -- believed to be the Russian…
