Communications of the ACM

The blog archive provides access to past blog postings from Communications of the ACM and other sources by date.
January 2018
From insideHPC
Job of the Week: Research Scientist specializing in HPC Processor Architectures at Jülich

 The Jülich Supercomputing Centre (JSC) is one of the three national supercomputing centres in Germany. It is partnering with leading technology providers on co-design hardware architectures for future supercomputers. In this…
The Jülich Supercomputing Centre (JSC) is one of the three national supercomputing centres in Germany. It is partnering with leading technology providers on co-design hardware architectures for future supercomputers. In this…
From insideHPC
Intel MKL Speeds Up Small Matrix-Matrix Multiplication for Automatic Driving

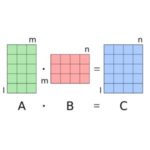 Certain applications, such as automated driving, require low latency small matrix-matrix multiplication in real time. They use specialized libraries that can be customized for small matrix operations. Recompiling and linking
…
Certain applications, such as automated driving, require low latency small matrix-matrix multiplication in real time. They use specialized libraries that can be customized for small matrix operations. Recompiling and linking
…
From The Eponymous Pickle
Alibaba Partnering with Kroger?

Tech integrations would be interesting here.
Kroger said to discuss Alibaba partnership
E-commerce giant also operates supermarkets in China
By Mark Hamstra in Supermarket News
Kroger Co. has held preliminary talks about a possible…
From insideHPC
Accelerating HPC Programmer Productivity with OpenACC and CUDA Unified Memory

 Doug Miles from NVIDIA gave this talk at SC17. "CUDA Unified Memory for NVIDIA Tesla GPUs offers programmers a unified view of memory on GPU-accelerated compute nodes. The CPUs can access GPU high-bandwidth memory directly, the…
Doug Miles from NVIDIA gave this talk at SC17. "CUDA Unified Memory for NVIDIA Tesla GPUs offers programmers a unified view of memory on GPU-accelerated compute nodes. The CPUs can access GPU high-bandwidth memory directly, the…
From My Biased Coin
Some Notes on "Learned Bloom Filters"

About a month ago, a draft paper was put out on arxiv called The Case for Learned Indexed Structures by the people at Google Brain. The paper has received some significant attention, perhaps because of its pedigree and perhaps…
From The Eponymous Pickle
Anki Cozmo Robot

More personable toy robotics. Not a new thing, but getting us more used to the concept.
Big brain. Bigger personality.
Say hello to Cozmo, a gifted little guy with a mind of his own. He’s a real-life robot like you’ve only seen…
From The Eponymous Pickle
Gathering Image data in 360

A kind of life logging model, or just image information gathering in 360 degrees
FITT360 is a 360-degree camcorder you wear around your neck
By Nicole Lee, @nicole in Engadget
Imagine if you could snap 360 degree photos and videos…
From Schneier on Security
WhatsApp Vulnerability

A new vulnerability in WhatsApp has been discovered: ...the researchers unearthed far more significant gaps in WhatsApp's security: They say that anyone who controls WhatsApp's servers could effortlessly insert new people into…
From BLOG@CACM
Beyond Folk Pedagogy

On evidence-based teaching.
From Putting People First
[Study] Rethinking The Smart City – Democratizing Urban Technology
![[Study] Rethinking The Smart City – Democratizing Urban Technology](/system/assets/0000/1953/030209_Vanderbeeken_Mark_250.small_square.jpg?1476779420&1260281963)
 Rethinking The Smart City – Democratizing Urban Technology By Evgeny Morozov and Francesca Bria Rosa Luxemburg Stiftung, New York Office January 2018 Download pdf: English version – German version Following the celebration of…
Rethinking The Smart City – Democratizing Urban Technology By Evgeny Morozov and Francesca Bria Rosa Luxemburg Stiftung, New York Office January 2018 Download pdf: English version – German version Following the celebration of…
From Putting People First
[Study] Rethinking The Smart City – Democratizing Urban Technology
![[Study] Rethinking The Smart City – Democratizing Urban Technology](/system/assets/0000/1953/030209_Vanderbeeken_Mark_250.small_square.jpg?1476779420&1260281963)
 Rethinking The Smart City – Democratizing Urban Technology By Evgeny Morozov and Francesca Bria Rosa Luxemburg Stiftung, New York Office January 2018 Download pdf: English version – German version Following the celebration of…
Rethinking The Smart City – Democratizing Urban Technology By Evgeny Morozov and Francesca Bria Rosa Luxemburg Stiftung, New York Office January 2018 Download pdf: English version – German version Following the celebration of…
From The Eponymous Pickle
Image Information for Learning in Context

Useful cognitive solutions will need to be taught, and thus need to to learn in changing contexts. Today we re-teach most systems to adjust them to changes in environments. The ultimate kind of augmentation. Images in context…
From Apophenia
Panicked about Kids’ Addiction to Tech? Here are two things you could do

Flickr: Jan Hoffman (This was originally posted on NewCo Shift) Ever since key Apple investors challenged the company to address kids’ phone addiction, I’ve gotten a stream of calls asking me to comment on the topic. Mostly,…
From Computer Science Teachers Association
How Far We’ve Come – and How Far We Have To Go

Roughly ten years ago, the US computing community first started to really address policy about teaching K-12 computer science. The ACM Education Policy Committee was formed with K-12 education as its focus, and a few people –…
From The Noisy Channel
Great post, and thanks for the shout-out! Excited to read the rest of the series.

Great post, and thanks for the shout-out! Excited to read the rest of the series.
From insideHPC
CloudLightning Project Report: The Future of HPC in the Cloud

 Today the CloudLightning project released a new report entitled: The Future of HPC in the Cloud. "Based upon the critical issues and problems identified through this research, industry, researchers and policymakers can more accurately…
Today the CloudLightning project released a new report entitled: The Future of HPC in the Cloud. "Based upon the critical issues and problems identified through this research, industry, researchers and policymakers can more accurately…
From The Noisy Channel
Faceted Search

Faceted search is a topic broad enough to deserve its own book. It has become a standard feature of all modern search engines, including open-source platforms like Solr and Elastic.
In this post, I’ll quickly explain how faceted…From The Eponymous Pickle
Linear Models and Forecasting

Useful thoughts on the topic. Being trained in this makes me think: Obviously. But confirmation bias is easy to jump to. Easier yet with complicated tools. And have also seen linearity misused.
Limits of Linear Models for…
From The Eponymous Pickle
Blockchain for Retail

Had conversation on this space recently and received some eye-rolling about the hype the space has received. Its not the same thing as the get rich quick world of 'Bit Coin', just uses the same underlying tech.,so deserves a…
From insideHPC
Video: HPC and the Tree of Life Project

 Jason Bond from Auburn University gave this talk at SC17 in Denver. "The Tree of Life Web Project (ToL) is a collaborative effort of biologists and nature enthusiasts from around the world. On more than 10,000 World Wide Web
…
Jason Bond from Auburn University gave this talk at SC17 in Denver. "The Tree of Life Web Project (ToL) is a collaborative effort of biologists and nature enthusiasts from around the world. On more than 10,000 World Wide Web
…
From insideHPC
CESNET Deploys Ciena Waveserver AI for Research

 Today CESNET announced the research community's first deployment of Ciena´s Waveserver Ai platform. The Czech research organization has interconnected GÉANT´s high-capacity routers using a 300 Gbps alien wavelength over 530km…
Today CESNET announced the research community's first deployment of Ciena´s Waveserver Ai platform. The Czech research organization has interconnected GÉANT´s high-capacity routers using a 300 Gbps alien wavelength over 530km…
From insideHPC
Tohoku University Liquid Cools HPC Systems with Asetek

 Today Asetek announced a new order from OEM partner Fujitsu for the Institute of Fluid Science at Tohoku University in Japan. The supercomputing system will consist of multiple computational sub-systems using the latest liquid…
Today Asetek announced a new order from OEM partner Fujitsu for the Institute of Fluid Science at Tohoku University in Japan. The supercomputing system will consist of multiple computational sub-systems using the latest liquid…
From insideHPC
Let’s Talk Exascale Podcast: ECP’s Application Assessment Project

 In this Let's Talk Exascale podcast, Kenny Roche from Pacific Northwest National Laboratory describes the ECP’s Application Assessment Project. "With Productivity, we’re aiming to coordinate how to improve software productivity…
In this Let's Talk Exascale podcast, Kenny Roche from Pacific Northwest National Laboratory describes the ECP’s Application Assessment Project. "With Productivity, we’re aiming to coordinate how to improve software productivity…
From Computational Complexity
How many degrees are in a Martian Year?
James Tanton gave a great talk at the JMM (Joint Math Meeting) in San Diego on
how many degrees are in a Martian Year?
but he didn't quite answer his title question. I found an excerpt of the talk on YouTube but still didn't…
From Schneier on Security
Detecting Drone Surveillance with Traffic Analysis

This is clever: Researchers at Ben Gurion University in Beer Sheva, Israel have built a proof-of-concept system for counter-surveillance against spy drones that demonstrates a clever, if not exactly simple, way to determine whether…
From The Eponymous Pickle
Empirical Software Engineering

Show us the numbers. Our of the science should come the measurable value.
Empirical Answers to Important Software Engineering Questions (Part 1 of 2) By Bertrand Meyer
" ... These studies have yielded many insights including…
From Gödel's Lost Letter and P=NP
Progress on the Frontier
An almost exponential improvement in bounds against ACC Source from previous paper Cody Murray is a PhD student of Ryan Williams at MIT. He and Ryan have a new paper that greatly improves Ryan’s separation of nonuniform circuits…
From The Eponymous Pickle
Chief Marketers View of AI

A marketing-eye view of AI. Again taking a very broad and limited definition of the term. Some of the ways are clearly deeply embedded in the tech we use today, so are they really new intelligence? Or rather augmentation…
From The Eponymous Pickle
Beijing gets an AI District

In TechnologyReview:
Beijing Is Getting a $2.1 Billion AI District:
China is gearing up to build a technology park in Beijing entirely dedicated to the development of artificial intelligence, news first reported by Xinhua, the
Master…
From BLOG@CACM
Empirical Answers to Important Software Engineering Questions (Part 2 of 2)

Time to start from what matters to practitioners
