Communications of the ACM

The blog archive provides access to past blog postings from Communications of the ACM and other sources by date.
February 2024
From Daniel Lemire's Blog
JSON Parsing: Intel Sapphire Rapids versus AMD Zen 4

Intel has release a new generation of server processors (Sapphire Rapids) while the latest AMD technology (Zen 4) is now broadly available. There are extensive comparisons available. Of particular interest is the open benchmark…
From BLOG@CACM
Niklaus Wirth and Beyond: Safeguarding the Intellectual Heritage of Computing

On preserving the memory, and work documentation, of the founders of computer science.
From Schneier on Security
No, Toothbrushes Were Not Used in a Massive DDoS Attack

The widely reported story last week that 1.5 million smart toothbrushes were hacked and used in a DDoS attack is false.
Near as I can tell, a German reporter talking to someone at Fortinet got it wrong, and then everyone else…From insideHPC
Dell: Omnia Copes with the Complexity of Configuring HPC-AI Environments

 [SPONSORED GUEST ARTICLE] Computer scientist Alan Perlis said fools ignore complexity while pragmatists suffer it. But when it comes to the complexity of configuring HPC, AI and data analytics environments, Perlis might say
…
[SPONSORED GUEST ARTICLE] Computer scientist Alan Perlis said fools ignore complexity while pragmatists suffer it. But when it comes to the complexity of configuring HPC, AI and data analytics environments, Perlis might say
…
From CS4FN (Computer Science For Fun)
Lego Computer Science: Turing Machines Part 3: the program

by Paul Curzon, Queen Mary University of London We have so far built the hardware of a Lego Turing Machine. Next we need the crucial part: software. It needs a program to tell it what to do. Our Turing Machine so far has an Infinite…
From insideHPC
EuroHPC Issues Call to Host Industrial Supercomputers: March 4 Deadline

 Feb. 8, 2024 — The EuroHPC Joint Undertaking (EuroHPC JU) has launched a call for expression of interest to select hosting entities for industrial-grade supercomputers, which will be acquired by the EuroHPC JU together with a…
Feb. 8, 2024 — The EuroHPC Joint Undertaking (EuroHPC JU) has launched a call for expression of interest to select hosting entities for industrial-grade supercomputers, which will be acquired by the EuroHPC JU together with a…
From insideHPC
Sylabs Announces SingularityCE 4.1.0

 Reno, NV – (February 8, 2024) – Sylabs, a provider of tools and services for performance-intensive container technology, announced the release of SingularityCE 4.1.0, the newest iteration of its container solution optimized for…
Reno, NV – (February 8, 2024) – Sylabs, a provider of tools and services for performance-intensive container technology, announced the release of SingularityCE 4.1.0, the newest iteration of its container solution optimized for…
From Schneier on Security
On Software Liabilities

Over on Lawfare, Jim Dempsey published a really interesting proposal for software liability: “Standard for Software Liability: Focus on the Product for Liability, Focus on the Process for Safe Harbor.”
Section 1 of this paper…From insideHPC
IBM AIU SoC Cluster to be Installed at Univ. of Albany

 IBM's long, slow climb back into advanced computing prominence took a turn yesterday with news from the University at Albany that it will be the first academic institution to receive a prototype computing cluster based on IBM's…
IBM's long, slow climb back into advanced computing prominence took a turn yesterday with news from the University at Albany that it will be the first academic institution to receive a prototype computing cluster based on IBM's…
From insideHPC
European Research Consortium Reports Sustainable Fuel Progress Using HPC

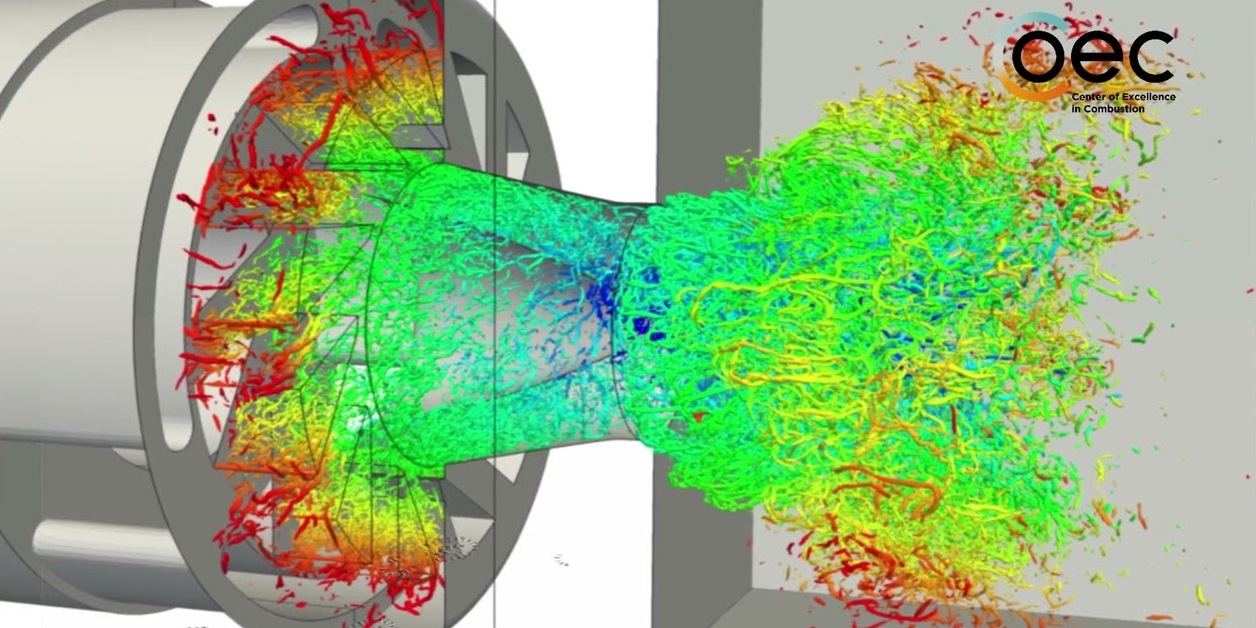 A European research consortium has announced progress in the development of sustainable fuels. CoEC reported what it said is a “notable breakthrough” linked to carbon-free hydrogen combustion. “…high-fidelity simulations were…
A European research consortium has announced progress in the development of sustainable fuels. CoEC reported what it said is a “notable breakthrough” linked to carbon-free hydrogen combustion. “…high-fidelity simulations were…
From Computational Complexity
Favorite Theorems: Graph Isomorphism
We start our favorite theorems of the last decade with a blockbuster improvement in a long-standing problem.
Graph Isomorphism in Quasipolynomial Time by László Babai
The graph isomorphism problem takes two graphs G and H both…From Schneier on Security
Teaching LLMs to Be Deceptive

Interesting research: “Sleeper Agents: Training Deceptive LLMs that Persist Through Safety Training“:
Abstract: Humans are capable of strategically deceptive behavior: behaving helpfully in most situations, but then behaving…From Putting People First
[Book] Avoiding the news
![[Book] Avoiding the news](/system/assets/0000/1953/030209_Vanderbeeken_Mark_250.small_square.jpg?1476779420&1260281963)
Drawing on interviews in Spain, the United Kingdom, and the United States as well as extensive survey data, the book explains why and how so many people consume little or no news despite unprecedented abundance and ease of access…
From Universal Acceptance Steering Group
UASG Publishes 2023 Universal Acceptance Activities Report

By the UASG 2023 was a milestone year for Universal Acceptance (UA). From local awareness and training sessions around the world to the inaugural UA Day, global support for and mobilization around UA reached unprecedented levels…
From The Computing Community Consortium Blog
CCC Responds to NIST RFI on Executing Tasks Assigned to NIST in the AI Executive Order

The CCC, on Friday of last week, responded to a Request for Information to assist NIST with executing the tasks assigned to them in the Executive Order on Safe, Secure, and Trustworthy Development and Use of Artificial Intelligence…
From insideHPC
Cisco and NVIDIA Partner on Integrated AI Infrastructure

 February 6, 2024 — Cisco and NVIDIA today announced plans to deliver AI infrastructure solutions for the data center designed to be easy to deploy and manage. “AI is fundamentally changing how we work and live, and history has…
February 6, 2024 — Cisco and NVIDIA today announced plans to deliver AI infrastructure solutions for the data center designed to be easy to deploy and manage. “AI is fundamentally changing how we work and live, and history has…
From insideHPC
Kathy Yelick to Deliver ISC 2024 Keynote on Post-Exascale Computing

 The opening keynote at the ISC 2024 conference in Hamburg will be delivered by Kathy Yelick, cice chancellor for research and the Robert S. Pepper Distinguished Professor of Electrical Engineering and Computer Sciences at the…
The opening keynote at the ISC 2024 conference in Hamburg will be delivered by Kathy Yelick, cice chancellor for research and the Robert S. Pepper Distinguished Professor of Electrical Engineering and Computer Sciences at the…
From BLOG@CACM
SWOT Analysis of ChatGPT in Computer Science Education

In this blog, we address high school teachers' perspective on the incorporation of ChatGPT into computer science education.
From insideHPC
Tenstorrent Selects Blue Cheetah Chiplet Interconnect IP for AI and RISC-V Solutions

 SUNNYVALE, Calif., Feb. 6, 2024 — Tenstorrent and Blue Cheetah Analog Design today announced that Tenstorrent has licensed Blue Cheetah’s die-to-die interconnect IP for its AI and RISC-V chiplet solutions. By selecting Blue
…
SUNNYVALE, Calif., Feb. 6, 2024 — Tenstorrent and Blue Cheetah Analog Design today announced that Tenstorrent has licensed Blue Cheetah’s die-to-die interconnect IP for its AI and RISC-V chiplet solutions. By selecting Blue
…
From Putting People First
Human-centered design to go beyond the mere “what customers want”

In a context of economic and geopolitical flux and volatility, a more in-depth human-centered design approach is now more necessary than ever, as it helps forward-looking companies to anticipate and be prepared for rapidly changing…
From Universal Acceptance Steering Group
UASG Announces Shortlisted Events for UA Day 2024

The Universal Acceptance Steering Group (UASG) has published the shortlisted events for the second annual Universal Acceptance (UA) Day, which will be held from March through the end of May and will feature 56 events spanning…
From insideHPC
QuEra to Build Quantum Testbed in UK

 BOSTON, February 5th, 2024 – Neutral-atom quantum company QuEra Computing has announced that the UK’s National Quantum Computing Centre (NQCC) at Harwell, Oxfordshire, will be home to a quantum computing testbed. Funded through…
BOSTON, February 5th, 2024 – Neutral-atom quantum company QuEra Computing has announced that the UK’s National Quantum Computing Centre (NQCC) at Harwell, Oxfordshire, will be home to a quantum computing testbed. Funded through…
From Schneier on Security
Deepfake Fraud

A deepfake video conference call—with everyone else on the call a fake—fooled a finance worker into sending $25M to the criminals’ account.
From CS4FN (Computer Science For Fun)
AMPER: AI helping future you remember past you

Research to develop a new AI tool to help people with dementia to remember, and gain confidence. Also includes some suggested classroom activities and examples of related types of jobs that people might do in this area, for careers…
From Daniel Lemire's Blog
How fast is rolling Karp-Rabin hashing?

A hash function maps values (e.g., strings) into a fixed number of strings, typically smaller than the original. It is useful to compare quickly two long strings, for example. Instead of comparing the strings, you may compare…
From Computational Complexity
The advantage of working on obscure things
I got an email from an organization that wants to publicize one of my papers. Which paper did they want to publicize?
1) If the organization was Quanta, they are KNOWN so I would trust it. Indeed, they have contacted me about…From CS4FN (Computer Science For Fun)
Lego Computer Science: Turing Machines Part 2: the controller

by Paul Curzon, Queen Mary University of London Last time we started to build a working computer out of Lego: a Turing Machine. So far we have seen that we can make the memory of a Turing Machine (its Infinite Tape) in Lego.Continue…
From Putting People First
[Book] Filterworld: how algorithms flattened culture
![[Book] Filterworld: how algorithms flattened culture](/system/assets/0000/1953/030209_Vanderbeeken_Mark_250.small_square.jpg?1476779420&1260281963)
From New Yorker staff writer Kyle Chayka comes a timely history and investigation of a world ruled by algorithms, which determine the shape of culture itself.
From Gödel's Lost Letter and P=NP
Predictions 2024
Would an AI-powered meta-prediction be smarter? Cropped from video source Punxsutawney Phil is our populace’s perennially perspicacious prognosticator. Every February 2, Groundhog Day, at dawn, he is summoned from his burrow…
From Schneier on Security
Friday Squid Blogging: Illex Squid in Argentina Waters

Argentina is reporting that there is a good population of illex squid in its waters ready for fishing, and is working to ensure that Chinese fishing boats don’t take it all.
As usual, you can also use this squid post to talk …