Communications of the ACM

The blog archive provides access to past blog postings from Communications of the ACM and other sources by date.
March 2017
From The Eponymous Pickle
Product Recommender in Python

More Python example than recommender. But also a useful view of programming in this domain. Via O'Reilly.
From Schneier on Security
Google Discloses Details of an Unpatched Microsoft Vulnerability

Google's Project Zero is serious about releasing the details of security vulnerabilities 90 days after they alert the vendors, even if they're unpatched. It just exposed a nasty vulnerability in Microsoft's browsers. This is…
From updated sporadically at best
Autoresponse: Striking: A Day Without a Woman

 |
| In front of the Federal Building, Pittsburgh. |
I am not responding to email on March 8, 2017 because I am observing A Day Without a Woman. In the afternoon, I will be joining students at CMU in a silent…
From insideHPC
Nvidia Brings AI to the Cloud with the HGX-1 Hyperscale GPU Accelerator

 Today, Microsoft, NVIDIA, and Ingrasys announced a new industry standard design to accelerate Artificial Intelligence in the next generation cloud. "Powered by eight NVIDIA Tesla P100 GPUs in each chassis, HGX-1 features an innovative…
Today, Microsoft, NVIDIA, and Ingrasys announced a new industry standard design to accelerate Artificial Intelligence in the next generation cloud. "Powered by eight NVIDIA Tesla P100 GPUs in each chassis, HGX-1 features an innovative…
From The Eponymous Pickle
Predicting Flash Floods with Weather Data

Good case Study from O'Reilly. I like the use of weather data, which can be problematic. Here converted to classification and thus prediction from embedded decision trees. Could have used the idea in a long ago US stream…
From The Eponymous Pickle
Superforecasting and Good Decision Makers

This is such an important issue. So many claims are made for good forecasting, but it is only as good as it is integrated into good decision making. Forecasting is an analytic method, but of little use if it can't contribute…
From insideHPC
Intel Joins iRODS Consortium to Better Integrate Lustre

 Today the integrated Rule-Oriented Data System (iRODS) Consortium announced that Intel Corporation has joined their membership-based foundation. "As a consortium member, Intel plans to improve integration between iRODS, the free…
Today the integrated Rule-Oriented Data System (iRODS) Consortium announced that Intel Corporation has joined their membership-based foundation. "As a consortium member, Intel plans to improve integration between iRODS, the free…
From The Computing Community Consortium Blog
NSF WATCH TALK- Securing the Network Time Protocol

The next WATCH talk, called Securing the Network Time Protocol is Thursday, March 16th, from 11 AM-12 PM EST. The presenter is Sharon Goldberg, an associate professor in the Computer Science Department at Boston University. Her…
From insideHPC
How GPU Hackathons Bring HPC to More Users

 "GPUs potentially offer exceptionally high memory bandwidth and performance for a wide range of applications. The challenge in utilizing such accelerators has been the difficulty in programming them. Enter GPU Hackathons; Our…
"GPUs potentially offer exceptionally high memory bandwidth and performance for a wide range of applications. The challenge in utilizing such accelerators has been the difficulty in programming them. Enter GPU Hackathons; Our…
From insideHPC
Will ECMWF Move Supercomputing to Italy?

 Weather and climate simulation services could soon be run in Europe rather than the UK as it was announced that the European Centre for Medium-range Weather Forecasts (ECMWF) is proposing to move its supercomputing capabilities…
Weather and climate simulation services could soon be run in Europe rather than the UK as it was announced that the European Centre for Medium-range Weather Forecasts (ECMWF) is proposing to move its supercomputing capabilities…
From Gödel's Lost Letter and P=NP
Is Computer Security Possible?
The breaks keep on coming… Holly Dragoo, Yacin Nadji, Joel Odom, Chris Roberts, and Stone Tillotson are experts in computer security. They recently were featured in the GIT newsletter Cybersecurity Commentary. Today, Ken and![]() …
…
From Schneier on Security
More on the CIA Document Leak

If I had to guess right now, I'd say the documents came from an outsider and not an insider. My reasoning: One, there is absolutely nothing illegal in the contents of any of this stuff. It's exactly what you'd expect the CIA…
From insideHPC
Compressing Software Development Cycles with Supercomputer-based Spark

 "Do you need to compress your software development cycles for services deployed at scale and accelerate your data-driven insights? Are you delivering solutions that automate decision making & model complexity using analytics
…
"Do you need to compress your software development cycles for services deployed at scale and accelerate your data-driven insights? Are you delivering solutions that automate decision making & model complexity using analytics
…
From Schneier on Security
The US Has Been Conducting Offensive Cyberattacks against North Korea

The New York Times is reporting that the US has been conducting offensive cyberattacks against North Korea, in an effort to delay its nuclear weapons program....
From insideHPC
Plan Your Travel and Stay For ISC 2017

 Registration is now open for the 32nd ISC High Performance conference. Attendees can save over 45 percent off the onsite registration fee by registering between now and May 10 for the full conference pass. "The organizers advise…
Registration is now open for the 32nd ISC High Performance conference. Attendees can save over 45 percent off the onsite registration fee by registering between now and May 10 for the full conference pass. "The organizers advise…
From The Eponymous Pickle
Who is winning at Monetizing AI?

I basically agree, though IBM leads now at the enterprise level, though it is still early. some supporting details at the link. I would also not eliminate startups from outside the list.
The race to monetize artificial intelligence…
From The Eponymous Pickle
IBM and Salesforce Partner with Watson

I agree with the statement that cognitive systems will continue to touch increasing numbers of people. If this will be by Watson, and how soon it will become universal, is still unclear. In TechCrunch:
IBM and Salesforce Partner…
From The Eponymous Pickle
Kuri Robot to Add Facial Recognition

Been following the claimed advances in the Kuri home robot, which now says it includes facial recognition and reaction. See their March Newsletter. Available for preorder, but no specific availability date yet. Had been
https…
From insideHPC
Registration Opens for ISC 2017 in Frankfurt

 Registration is now open for ISC 2017 with discounted Early Bird rates. As the largest high performance computing forum in Europe, ISC 2017 takes place June 18-22 in Frankfurt, Germany. "First held in 1986, ISC High Performance…
Registration is now open for ISC 2017 with discounted Early Bird rates. As the largest high performance computing forum in Europe, ISC 2017 takes place June 18-22 in Frankfurt, Germany. "First held in 1986, ISC High Performance…
From Computer Science Teacher - Thoughts and Information From Alfred Thompson
Infosys Foundation USA Asks Why Do You Make #WhyIMake

Thanks to a Facebook link I found a video interview created by Infosys Foundation USA. on why he “makes.” This lead to one with Adam Savage of mythbuster fame on the same topic.Infosys Foundation USA. is asking other people to…
From The Computing Community Consortium Blog
Call for Proposals: Creating Visions for Computing Research

The mission of Computing Research Association’s (CRA) Computing Community Consortium (CCC) is to catalyze the computing research community and enable the pursuit of innovative, high-impact research. CCC conducts activities that…
From insideHPC
SDSC Seismic Simulation Software Exceeds 10 Petaflops on Cori Supercomputer

 Researchers at SDSC have developed a new seismic software package with Intel Corporation that has enabled the fastest seismic simulation to-date. SDSC’s ground-breaking performance of 10.4 Petaflops on earthquake simulations
…
Researchers at SDSC have developed a new seismic software package with Intel Corporation that has enabled the fastest seismic simulation to-date. SDSC’s ground-breaking performance of 10.4 Petaflops on earthquake simulations
…
From The Eponymous Pickle
On Genuine Smiles

In Inc: Smiles, real and fake. The Duchenne smile was tested for machine interaction and positive reaction to products.
Examined for possible use in how people react to products ....
The Duchenne smile as indicator of genuine…
From insideHPC
Fujitsu & Linaro Collaborate to Accelerate HPC on ARM

 “Developing a supercomputer that is many times faster than any of those currently available is clearly a challenging process and involves leveraging Fujitsu’s top hardware and software talent, as well as the help of partner companies…
“Developing a supercomputer that is many times faster than any of those currently available is clearly a challenging process and involves leveraging Fujitsu’s top hardware and software talent, as well as the help of partner companies…
From Daniel Lemire's Blog
College and inequality

Most college professors are squarely on the left ideologically. They believe that part of their mandate is to reduce inequality, by helping to provide college degrees to all who qualify. This always felt as strange to me. Higher…
From The Eponymous Pickle
Kroger Testing Uber for Delivery

Discussion on Kroger and Uber in Retailwire:
Will using Uber for home deliveries work for Kroger? by George Anderson
Kroger’s streak of quarterly same-store gains has ended after 13 years, but the supermarket giant is intent on…
From insideHPC
HPE to Acquire Nimble Storage

 Today Hewlett Packard Enterprise announced an agreement to acquire Nimble Storage, the California-based provider of predictive all-flash and hybrid-flash storage solutions. HPE will pay $12.50 per share in cash, representing
…
Today Hewlett Packard Enterprise announced an agreement to acquire Nimble Storage, the California-based provider of predictive all-flash and hybrid-flash storage solutions. HPE will pay $12.50 per share in cash, representing
…
From Schneier on Security
WikiLeaks Releases CIA Hacking Tools

WikiLeaks just released a cache of 8,761 classified CIA documents from 2012 to 2016, including details of its offensive Internet operations. I have not read through any of them yet. If you see something interesting, tell us in…
From insideHPC
Optimizing Vehicle Design with Simulation

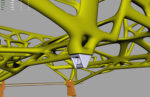 The use of simulation software for validation and testing is a well established process for many engineering companies – but advances in software, combined with increased pressure from competition and regulatory requirements,…
The use of simulation software for validation and testing is a well established process for many engineering companies – but advances in software, combined with increased pressure from competition and regulatory requirements,…
From Schneier on Security
Building Smarter Ransomware

Matthew Green and students speculate on what truly well-designed ransomware system could look like: Most modern ransomware employs a cryptocurrency like Bitcoin to enable the payments that make the ransom possible. This is perhaps…
