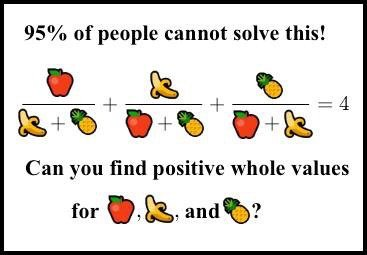Communications of the ACM

The blog archive provides access to past blog postings from Communications of the ACM and other sources by date.
April 2024
From Schneier on Security
xz Utils Backdoor

The cybersecurity world got really lucky last week. An intentionally placed backdoor in xz Utils, an open-source compression utility, was pretty much accidentally discovered by a Microsoft engineer—weeks before it would haveArsTehnica…
From The Computing Community Consortium Blog
CCC NTIA RFI Response

Last week, the CCC responded to the National Telecommunications and Information Administration’s Request for Information on Dual Use Foundation Artificial Intelligence Models with Widely Available Model Weights. The CCC’s own…
From Schneier on Security
Declassified NSA Newsletters

Through a 2010 FOIA request (yes, it took that long), we have copies of the NSA’s KRYPTOS Society Newsletter, “Tales of the Krypt,” from 1994 to 2003.
There are many interesting things in the 800 pages of newsletter. There are…From The Noisy Channel
Analyzing the AI Search Opportunity

In the past several years, AI has disrupted every part of the technology industry. Search applications are no exception: it is not a question of whether to use AI for search, but where to incorporate it into the stack. In this…
From Computational Complexity
A Math Question and a Meta Question
1) Question: find x,y,z natural numbers such that the following is true:
$$ \frac{x}{y+z} + \frac{y}{x+z} + \frac{z}{x+y} = 4. $$
I was first presented the problem a more fun way:
From Schneier on Security
Magic Security Dust

Adam Shostack is selling magic security dust.
It’s about time someone is commercializing this essential technology.